MAC Based on Block Ciphers: DAA and ÇMAC
How CMAC Works
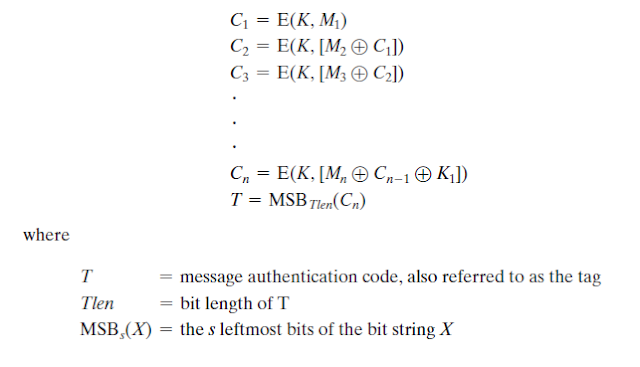
CMAC operates on messages of arbitrary length, splitting them into fixed-size blocks and processing them with the block cipher. The last block is handled specially depending on the message length.
Step-by-Step Process:
Message Splitting and Padding:
- The input message
Mis split intonblocks of fixed size (e.g., 128-bit blocks for AES). If the message length is not a multiple of the block size, the last block is padded using a special padding rule. - Padding typically appends a "1" bit followed by enough "0" bits to make the block the required size.
- The input message
Subkey Generation: Two subkeys (
K1andK2) are generated from the original keyKusing the block cipher. These subkeys will be used to handle the last block of the message:- Subkey
K1is derived by encrypting a block of zeros with the block cipher and performing some bitwise operations. - Subkey
K2is derived by shiftingK1and applying modular arithmetic, which depends on the size of the block cipher (like AES).
- Subkey
Processing the Blocks: The message blocks are processed one at a time with the block cipher:
- For each block except the last, the block is XORed with the result of the previous block's encryption and then encrypted with the block cipher.
- The last block is handled differently based on whether the message length is a multiple of the block size:
- If the last block is complete (i.e., no padding is needed), it is XORed with subkey
K1before encryption. - If the last block is incomplete (i.e., padding is required), it is padded, XORed with subkey
K2, and then encrypted.
- If the last block is complete (i.e., no padding is needed), it is XORed with subkey
Final Output: The result of the last encryption step is the CMAC value, which is a fixed-length output (equal to the block size of the cipher, such as 128 bits for AES). This MAC is used to verify the integrity and authenticity of the message.
- Strong Message Integrity: CMAC ensures that even a small modification in the message results in a completely different MAC, making it easy to detect tampering.
- Message Authentication: Only someone with the correct secret key can generate or verify the CMAC, ensuring the authenticity of the message.
- Collision Resistance: Since it is based on secure block ciphers like AES, CMAC is resistant to collision attacks (where two different messages produce the same MAC).
- Key Strength: The strength of CMAC depends on the strength of the block cipher and the size of the key (e.g., AES-128, AES-192, AES-256).
Applications of CMAC
- Secure Communication Protocols: CMAC is used in protocols such as IEEE 802.11 (Wi-Fi), IPsec, and others for message authentication.
- Authentication Codes in Cryptographic Systems: CMAC is used to verify the integrity and authenticity of messages in various cryptographic systems.
- Data Integrity Checks: It can be used in systems that require strong data integrity checks, especially where performance is important.
Conclusion
CMAC is a highly secure and efficient method for message authentication, based on the use of block ciphers like AES. Its strength comes from the security of the underlying block cipher, making it a robust choice for applications that need both data integrity and authenticity. Since it is standardized and well-supported, CMAC is widely used in secure communication protocols and cryptographic systems.



Comments
Post a Comment