Substitution Ciphers-Caesar Cipher
A substitution technique is one in which the letters of plaintext are replaced by other letters or by numbers or symbols.If the plaintext is viewed as a sequence of bits, then substitution involves replacing plaintext bit patterns with ciphertext bit patterns.
Caesar Cipher
The earliest known, and the simplest, use of a substitution cipher was by Julius Caesar.The Caesar cipher involves replacing each letter of the alphabet with the letter standing three places further down the alphabet.
For example,
plain text : meet me after the toga party
cipher text : PHHW PH DIWHU WKH WRJD SDUWB
Note that the alphabet is wrapped around, so that the letter following Z is A.We can define the transformation by listing all possibilities, as follows:
plain text : a b c d e f g h i j k l m n o p q r s t u v w x y z
cipher text : D E F G H I J K L M N O P Q R S T U V W X Y Z A B C
Let us assign a numerical equivalent to each letter:
Then the algorithm can be expressed as follows. For each plaintext letter $p$, substitute the ciphertext letter $C$:
$$C=E(3,p)=(p+3) \pmod {26}$$
A shift may be of any amount, so that the general Caesar algorithm is
$$C=E(k,p)=(p+k) \pmod {26}$$
where $k$takes on a value in the range 1 to 25.The decryption algorithm is simply
$$p=D(k,C)=C-k \pmod{26}$$
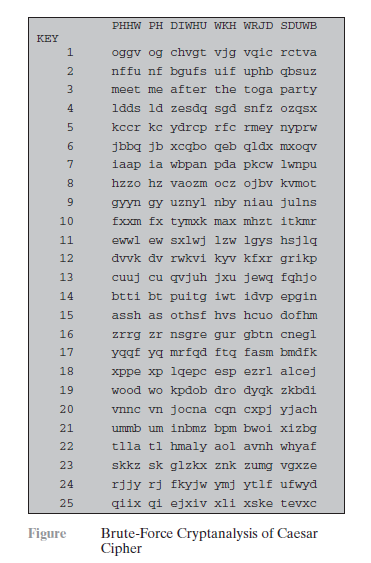
If it is known that a given ciphertext is a Caesar cipher, then a brute-force cryptanalysis is easily performed: simply try all the 25 possible keys. Figure below shows the results of applying this strategy to the example ciphertext. In this case, the plaintext leaps out as occupying the third line.
Three important characteristics of this problem enabled us to use a bruteforce cryptanalysis:
1. The encryption and decryption algorithms are known.
2. There are only 25 keys to try.
3. The language of the plaintext is known and easily recognizable.
In most networking situations, we can assume that the algorithms are known.What generally makes brute-force cryptanalysis impractical is the use of an algorithm that employs a large number of keys. For example, the triple DES algorithm, makes use of a 168-bit key, giving a key space of or greater than $3.7 \times 10^{50}$ possible keys.
The third characteristic is also significant. If the language of the plaintext is unknown, then plaintext output may not be recognizable. Furthermore, the input may be abbreviated or compressed in some fashion, again making recognition difficult. For example, Figure below shows a portion of a text file compressed using an algorithm called ZIP. If this file is then encrypted with a simple substitution cipher (expanded to include more than just 26 alphabetic characters), then the plaintext may not be recognized when it is uncovered in the brute-force cryptanalysis.
Python Code Caesar Cipher
def encrypt_caesar_cipher(text, shift):
"""Encrypts the text using Caesar cipher with a given shift."""
encrypted_text = ""
for char in text:
if char.isalpha():
# Determine if the character is uppercase or lowercase
start = ord('A') if char.isupper() else ord('a')
# Calculate the new position after the shift
new_position = (ord(char) - start + shift) % 26
# Append the encrypted character to the result
encrypted_text += chr(start + new_position)
else:
# Non-alphabetic characters are not changed
encrypted_text += char
return encrypted_text
def decrypt_caesar_cipher(encrypted_text, shift):
"""Decrypts the text using Caesar cipher with a given shift."""
return encrypt_caesar_cipher(encrypted_text, -shift)
# Example usage
plaintext = "Hello, World!"
shift = 3
encrypted = encrypt_caesar_cipher(plaintext, shift)
print(f"Encrypted: {encrypted}")
decrypted = decrypt_caesar_cipher(encrypted, shift)
print(f"Decrypted: {decrypted}")
Output
Encrypted: Khoor, Zruog!
Decrypted: Hello, World!
Python Code Brute force Attack on Caesar Cipher
def brute_force_caesar_cipher(ciphertext):
"""Attempts to decrypt the ciphertext by trying all possible Caesar cipher shifts."""
possible_plaintexts = []
for shift in range(26):
decrypted_text = ""
for char in ciphertext:
if char.isalpha():
# Determine if the character is uppercase or lowercase
start = ord('A') if char.isupper() else ord('a')
# Calculate the new position after reversing the shift
new_position = (ord(char) - start - shift) % 26
# Append the decrypted character to the result
decrypted_text += chr(start + new_position)
else:
# Non-alphabetic characters are not changed
decrypted_text += char
possible_plaintexts.append(decrypted_text)
return possible_plaintexts
# Example usage
ciphertext = "Khoor, Zruog!"
# Perform the brute force attack
results = brute_force_caesar_cipher(ciphertext)
# Display the results
for i, plaintext in enumerate(results):
print(f"Shift {i}: {plaintext}")
Output
Shift 0: Khoor, Zruog!
Shift 1: Jgnnq, Yqtnf!
Shift 2: Ifmmp, Xpsme!
Shift 3: Hello, World!
Shift 4: Gdkkn, Vnqkc!
Shift 5: Fcjjm, Umpjb!
Shift 6: Ebiil, Tloia!
Shift 7: Dahhk, Sknhz!
Shift 8: Czggj, Rjmgy!
Shift 9: Byffi, Qilfx!
Shift 10: Axeeh, Phkew!
Shift 11: Zwddg, Ogjdv!
Shift 12: Yvccf, Nficu!
Shift 13: Xubbe, Mehbt!
Shift 14: Wtaad, Ldgas!
Shift 15: Vszzc, Kcfzr!
Shift 16: Uryyb, Jbeyq!
Shift 17: Tqxxa, Iadxp!
Shift 18: Spwwz, Hzcwo!
Shift 19: Rovvy, Gybvn!
Shift 20: Qnuux, Fxaum!
Shift 21: Pmttw, Ewztl!
Shift 22: Olssv, Dvysk!
Shift 23: Nkrru, Cuxrj!
Shift 24: Mjqqt, Btwqi!
Shift 25: Lipps, Asvph!
Eve has interpreted the cipher text "UVACLYFZLJBYL .Show how she can use an exhaustive key search to break this Caesar cipher. (University Question)
Shift 0: UVACLYFZLJBYL
Shift 1: TUZBKXEYKIAXK
Shift 2: STYAJWDXJHZWJ
Shift 3: RSXZIVCWIGYVI
Shift 4: QRWYHUBVHFXUH
Shift 5: PQVXGTAUGEWTG
Shift 6: OPUWFSZTFDVSF
Shift 7: NOTVERYSECURE
Shift 8: MNSUDQXRDBTQD
Shift 9: LMRTCPWQCASPC
Shift 10: KLQSBOVPBZROB
Shift 11: JKPRANUOAYQNA
Shift 12: IJOQZMTNZXPMZ
Shift 13: HINPYLSMYWOLY
Shift 14: GHMOXKRLXVNKX
Shift 15: FGLNWJQKWUMJW
Shift 16: EFKMVIPJVTLIV
Shift 17: DEJLUHOIUSKHU
Shift 18: CDIKTGNHTRJGT
Shift 19: BCHJSFMGSQIFS
Shift 20: ABGIRELFRPHER
Shift 21: ZAFHQDKEQOGDQ
Shift 22: YZEGPCJDPNFCP
Shift 23: XYDFOBICOMEBO
Shift 24: WXCENAHBNLDAN
Shift 25: VWBDMZGAMKCZM
Use an additive cipher to encrypt the message "CRYPTOGRAPHY" using the key k=19 in modulus 26. ( University Question )
Encrypted: VKRIMHZKTIAR



Comments
Post a Comment